We're all used to seeing "Log in with Facebook" or "Log in with Google" at sites around the Internet — or less frequently, an offer to log in with Twitter, LinkedIn or Pinterest. It's a common option at news sites like CNN.com and the UK's Guardian newspaper, music streaming services such as Spotify and tens of thousands of other online retailers, apps and games.
Logging in with a main account whose credentials you easily remember saves you the trouble of going through yet another laborious account creation and memorizing dozens of passwords. It allows you to easily post about something you've just read or bought.
But what exactly are you signing up for?
Requesting your data
Logging in to a website using a service such as Facebook or Google allows the website to make a request for data about you. Facebook and LinkedIn have quite a lot of data available for request: your birthday, friends list, email address, employment, colleges attended, photos and information that your friends have posted about you (for example, tagged photos). Other services like Twitter don't possess the same level of personal data about its users and aren't able to turn over as much information.
The exact data that the website is requesting pops up in a window asking for permission. Saying yes to that request adds one more tiny bridge between the virtual islands of your online self.
This seemingly small agreement can carry larger repercussions. Linking two or more sites allows companies to collect more data, building an increasingly rounded profile about you. Allowing one account to have access to others means that if the least secure account is hacked, the rest could also be compromised.
Facebook and Google are by far the two most frequently used services for logging in to other sites. Facebook snared 62% of all social log-ins across the tens of thousands of sites that support it (as of the end of 2015); Google is used 24% of the time according to Gigya, a customer identity management company.
Social networks want to be a trusted source for verifying your identify. In fact, at the Facebook developers conference this year, the company announced a service called Delegated Account Recovery, which would let you use Facebook to verify your identity if you forget your password on an app or website.
Yet social networks don't inherently have value as a trusted source of identity. Privacy is not the main concern of a social network; like any for-profit company, its focus is on monetizing its product.
We are the product. Take Facebook; according the eMarketer, Facebook is expected to generate $16.33 billion in net digital ad revenue in the U.S. market this year and Google is expected to generate $5.24 billion in display ads in the U.S.
What happens to your data
The data held by social platforms and service providers like Google covers your habits and preferences. Facebook Like buttons littered throughout the Internet bounce back data about products or articles you've liked, while the Facebook Open Graph platform for other sites comes with plug-ins that collect data such as which of your friends already use a particular website or what you do while on the site.
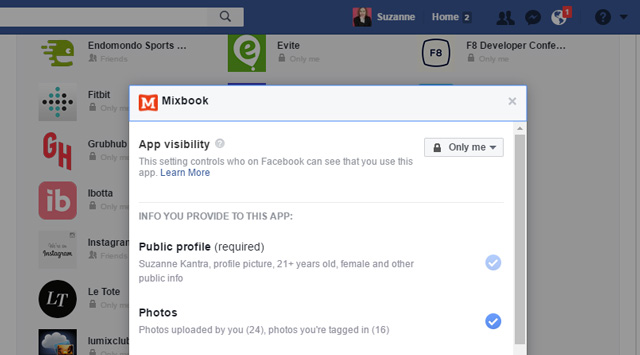
In response to privacy concerns, Facebook does allow you to log in to third-party apps without having to give permission to share personal details like your name, email, birthday and so forth. Make sure you sever the connection for apps you're not longer using. You can do that by going to Facebook Settings (click on the down arrow next to the question mark in the upper right) and select Apps. On that page you can click on any app and see the information the app has access to and can change those access privileges.
Google tracks your online habits through search queries, its Chrome browser and more, building demographic profiles it then sells to companies who want to buy advertising on Google products, from Gmail sidebar ads to sponsored search results.
The more data ecosystems that are connected, the more a company can know about us and the more we continue be their product, helping to maximize their profits.
The social log-in is another way of adding data ecosystems to the company's reach. Down the line, it could cue an era of increasingly uncanny ad targeting, in line with the infamous example of Target analyzing a teenager's purchasing habits to deduce she was pregnant.
As for those Terms of Service agreements that detail what will and won't happen to your personal data: How many privacy changes on Facebook have you agreed to without understanding what they're changing? The terms of services are changing all the time as Facebook evolves. In addition to reading the terms of service when they change, make sure you check your privacy settings regularly. Click on the question mark in the
Security matters
Signing into several sites with the one log-in can leave accounts as vulnerable as the one with the lowest security. So-called daisy-chained accounts can also make identity theft easier for would-be scammers.
If a trusted source of your identity is less secure — whether that's Facebook, Google or another account — they risk becoming the weak link in the chain that gets targeted by attackers.
There's also the possibility that less scrupulous sites may do something else with your data than what you agreed to — for example, selling it to a third or fourth company that you do not want holding any aspect of your online identity. Before you sign into a site with your existing social account, make sure your trust the third-party site.
The rules of logging in
People use Facebook and Google log-in because it's easier than creating a new account. The benefits of sailing smoothly past log-ins and account registrations often mean we're happy to trade away some data privacy.
- Be aware that if you choose to log in with a social account, your data will be shared between the social network and the third-party app. Stay updated on your social networks' privacy policies, and use the social log-in accordingly at sites you feel comfortable sharing data with.
- Don't use your main account to log in to a site whose security you don't trust.
- Don't link a social profile to sensitive info like your Social Security number or financial details. In these cases, a separate account and password is your safest bet.
The most secure use of social log-ins is with closely related sites. For example, Twitter's log-in works well with services it's integrated with its own ecosystem or where there's a benefit to being able to cross-post — say, between Wordpress and Twitter. Likewise, Facebook could be used for services such as Instagram, Facebook Apps or other third-party services that plug in to the Facebook platform.
Updated 5/6/2017
[Google Facebook login image via OlegDoroshin / Shutterstock.com]
















From Davìď frost on October 22, 2016 :: 6:27 pm
Can I login to goggle through Facebook
Reply
From Captain Obvious on October 21, 2019 :: 11:06 am
Goggle, yes. Google - no.
Reply