We warned you about fake CAPTCHAs last fall, and now the threat has evolved. What started as a clever Windows-targeted malware trap has turned into a full-blown, cross-platform scam operation that’s tricking millions of people into installing malware on their own devices.
Cybercriminals are exploiting our familiarity with CAPTCHAs – those little checkboxes or image puzzles we’ve all clicked without a second thought. In these scams, a fake CAPTCHA appears on a compromised or spoofed website, prompting you to "verify" you're human. But instead of stopping bots, the page guides you through a series of deceptive steps that end with malware being installed on your system, by you.
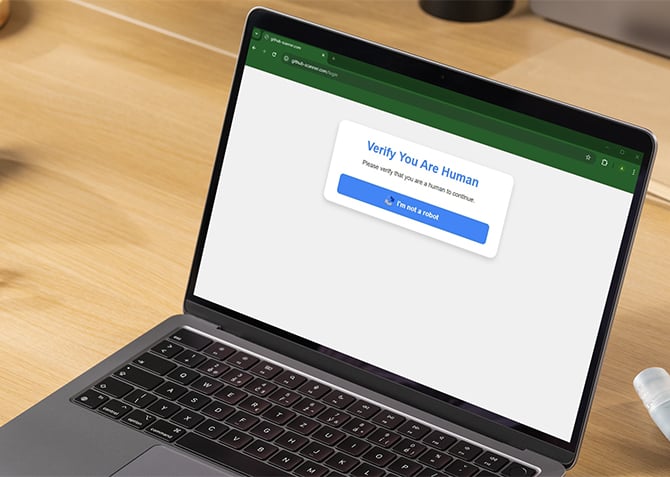
When we first investigated this last year, we tested one of these pages using a URL flagged by security journalist Brian Krebs. It looked disturbingly real. After clicking through the fake CAPTCHA, I was prompted to hit Windows+R, paste a command, and press Enter. That launched a PowerShell script that downloaded Lumma Stealer, a nasty piece of malware that targets crypto wallets, saved passwords, financial data, and even email and messaging accounts. The whole process felt smooth and almost routine, which is exactly why it works.
In Partnership with Surfshark
The Q1/2025 Gen Threat Report confirms that this attack pattern hasn’t just persisted – it’s gotten worse. More than 4 million people were protected from “Scam-Yourself Attacks” like FakeCaptcha last quarter alone. And this time, it’s not just Windows users being targeted. New versions now affect macOS, using fake verification steps to install AMOS (Atomic Stealer), a cross-platform info-stealer. One version even hides malware in an MP3 file, with JavaScript embedded and executed via a legitimate system tool. It’s clever, and it's working.
What’s truly dangerous about these scams is that they don’t feel like malware. They feel like a normal interaction. You’re never asked to download a file with a sketchy name – you’re asked to do something that feels routine. That’s the trick. These scams succeed not because they’re technically sophisticated, but because they hijack habits we’ve learned to trust.
Read more: How AI Crypto Influencers on YouTube Are Stealing Real Money
If a CAPTCHA ever asks you to run a command, download a file, or perform steps beyond clicking boxes or selecting images, don’t do it. Close the page and walk away. And if you haven’t already, make sure you’re running robust, up-to-date antimalware software. In our own testing, Bitdefender, which we use and recommend Bitdefender caught Lumma Stealer before it could fully execute. It’s a stark reminder of how important that safety net really is.
[Image credit: Screenshot via Techlicious, mockup of laptop via Canva]
