There's a good chance that hackers know at least one of your passwords. Last year, Yahoo announced that hackers managed to steal three billion — yes, billion — email addresses and passwords that belonged to users on Yahoo, Tumblr, Flickr and more. And Yahoo is hardly the only big business that's fallen victim to hackers. Last year alone there were more than 1,300 data breaches, any of which could have put your personal information in the hands of hackers.
And while you may not care that your unused Yahoo account was hacked, having your password stolen can be a real problem. Why? Because despite security experts warning us not to, many of us use the same login and password for many different accounts — and when a hacker gets one of them, it's often easy to find others.
If you're trying to figure out whether or not you should be worried about your accounts being compromised, a site called haveibeenpwned.com can help. Despite the silly name, the site is completely legitimate, letting you quickly search to see if your email address or account names have shown up in these data breaches. If you haven't used it before, it's worth checking out and setting up notifications so you'll get an email if your accounts show up in a future data breach (just click "notify me" at the top of the page to sign up).
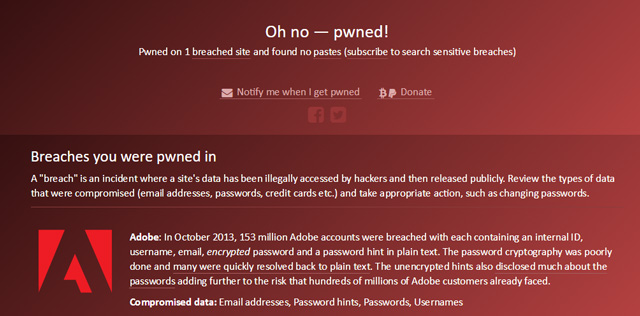
What's new is a tool that will tell you if your password — not just your account name — has been compromised. To find out if yours is on the list, just go to the site's password page and look yours up. And, yes, it's safe to do so on this site, which takes serious measures to protect your security. Just remember you should be extremely wary of unknown sites that ask for your password — a less trustworthy site could easily use this to steal your account information.
[Editor's note 3/8/18: Some people are questioning whether entering a password into this site creates its own security risks. The creator of the site, Troy Hunt, is a well-known and highly-regarded security expert; you are not entering any other information that could be used/associated with the password (e.g., user name, email, specific site name); and the site isn't storing your password. However, it is theoretically possible that if you sign up to be notified when a password is breached, the stored hash could somehow be decrypted, and if there is an IP address stored alongside it that decrypted password could then be connected back to you and your logins via other third-party hacks. We would say the likelihood of this is extremely thin, and the benefit of the site outweighs this risk, but it is possible. So if you want to be absolutely safe, only enter passwords that you are no longer using, or change any active passwords you do enter immediately before or after. There is still value to the process with inactive passwords because if one of those hacked passwords is the one you're using for your bank, email or other critical use, you know there's a possibility that either their data was hacked, you're reusing passwords and risking your critical site login or the passwords you're using are too common and you need to develop more secure password habits.]
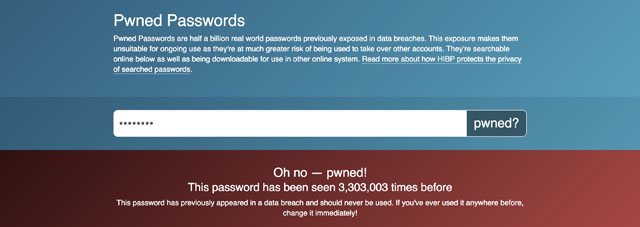
After you type in your password and hit enter, the site will tell you whether the password has shown up in any data breaches, and how many times. For example, the all too common "password" has shown up 3,303,003 in data breaches. Even if your usual password hasn't been leaked three million times, you should change it if it's been leaked at all — because once it's out there, it makes it easier for hackers to get into any accounts that use that password.
If you find out your passwords have been compromised, you should change them immediately. Be sure to make a different password for every site and use a password manager to keep track of them all. Our current favorite is Dashlane, which you can download for free.
Once you've changed any hacked passwords, it's time to turn on two-factor authentication for any accounts that offer it. This security feature means that in addition to your username and password, you'll need a code — often texted to your phone or sent to or sent to an app like Google Authenticator — to get into your account. This can stop hackers in their tracks even if they do have your username and password, but don't use it as an excuse not to change any compromised passwords. While the instructions for setting up two-factor authentication will be different for each site, you can check Two Factor Auth to find sites that support this security feature and how to enable it on each.
Now you can be sure your accounts are safe and stay safe in the future.
[Image credit: weak password via BigStockPhoto, haveibeenpwned.com]













From Khürt Williams on March 02, 2018 :: 8:23 am
> After you type in your password and hit enter, the site will tell you whether the password has shown up in any data breaches, and how many times.
+1 more time since you have just confirmed it with that site.
Reply
From Jon on March 02, 2018 :: 11:52 am
@Khürt Williams, you obviously don’t know anything about the haveibeenpwned site or its owner, Troy Hunt, a security researcher for Microsoft. Mr. Hunt has no interest in stealing your passwords. You can read more about him and his pawned passwords database here: https://www.troyhunt.com/ive-just-launched-pwned-passwords-version-2/
Reply
From Khürt Williams on March 05, 2018 :: 8:22 am
Let’s be clear. The owner is pwned is known. TO YOU! Let’s also be clear, suggesting that the public put their passwords AND email address into a website that will check if it’s been compromised is NOT a good thing to teach the general public.
Tony himself from the same link you provided.
>As much as I don’t want to encourage people to plug their real password(s) into random third-party sites, I can guarantee that a sizable number of people got a positive hit and then changed their security hygiene as a result.
Reply
From Josh Kirschner on March 02, 2018 :: 4:35 pm
Troy Hunt is a very well-known and highly respected security researcher. We fully trust his site or we wouldn’t recommend it. I feel more comfortable entering my passwords on haveibeenpwned.com than I do entering them into many of the actual sites I log into on a daily basis. Haveibeenpwned does not store the password you enter (it just crosschecks it against a known list of hacked passwords), nor is the password you’re checking associated with any other identifiable information, such as an email address or username.
Beyond that, there is great benefit to knowing whether the password(s) you’re currently using has already been hacked through a prior breach, and Haveibeenpwned offers a safe and easy way to do that - ignorance is not bliss when it comes to compromised credentials.
Reply
From Khürt Williams on March 05, 2018 :: 8:16 am
Let’s be clear. The owner is pwned is known. TO YOU! Let’s also be clear, suggesting that the public put their passwords into a website that will check if it’s been compromised is NOT a good thing to teach the general public.
Reply
From Khürt Williams on March 05, 2018 :: 8:25 am
Most companies have a policy requiring that employees change their password every 90 days. Instead of checking an online database, just change your personal passwords on a similar schedule and use a tool like 1Password.
Reply
From Josh Kirschner on March 05, 2018 :: 3:56 pm
It has become widely accepted in the security community, based on a number of academic research studies, that requiring regular/frequent password changes is counterproductive because it encourages users to choose easy-to-remember passwords and reuse those passwords across sites. The NIST recently recommended dropping password expiration in their latest security recommendations (http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63b.pdf), as does Bruce Schneier (https://www.schneier.com/blog/archives/2017/10/changes_in_pass.html), the FTC (https://www.ftc.gov/news-events/blogs/techftc/2016/03/time-rethink-mandatory-password-changes) and others (https://www.sans.org/security-awareness-training/blog/time-password-expiration-die). Users would be far better off creating a sufficiently complex passphrase that can be easily remember for each site and then just leaving it alone.