[Editor's note 5/28/2020: Since this article was written nine years ago, many new phone hacking methods have been developed and/or discovered. In addition, cell phone operating systems have evolved significantly. We've created a new article to cover those various hacks in our new story: How to Tell if Your Phone Has Been Hacked. Please go there for the latest information. We're keeping this story active for the issues and useful advice contained in the comments.]
You probably know there are plenty of apps you can install on your smartphone to track its location in case it gets lost or stolen. Apple's “Find My iPhone” is one good one and many security apps, such as AVG Mobilation, can track down a phone in seconds.
But what if someone else is tracking you? Is there any chance your boss or spouse could be spying on everything you do on your phone?
It’s easy to do. Spy apps are plentiful and can imperceptibly track text and e-mail messages, location, Web sites you visit, who you call and what photos and videos you shoot. The problem is these apps are difficult to detect and run invisibly in the background.
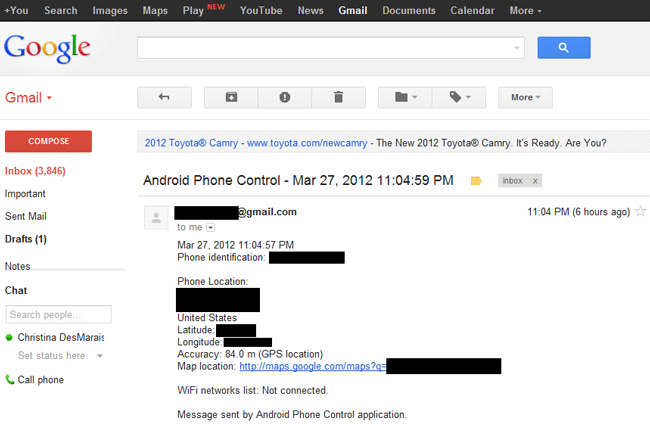
I decided to track my son and installed an app on his phone called Phone Control by Laucass (free on Google Play). Of course, secretly intercepting electronic communications without the person's knowledge and consent is illegal, so I told my son I was doing it and that I’d only use it if I had good reason.
Every day I receive emails that indicate my son’s location as he’s using his phone out in the world. I can click on those links in my email to see via Google Maps where he is (although I very rarely do). I could also set up the app to send me data about everything else he’s doing on his phone, but that’s not something I personally need—or want—to do.
Signs your phone may have been compromised
Someone borrowed or took your phone
I had to have my son’s phone in hand to install Android Phone Control. Once activated, however, there’s no icon in the application launcher. The app shows up with the name “Android System” in the applications manager so it doesn’t look suspicious. If you think someone could do something like this when you’re not paying attention or asleep, secure your phone with a passcode that isn’t easy to guess.
(Editor's Note 9/26/12: To confirm you have the spyware and not a standard Android app by the same name, follow these steps to open the spy app (dial the phone number.)
(Editor's Note 8/28/13: See our in-depth study of mobile security apps for more detail on 9 of the most common spyware programs and how to detect them.)
(Editor's Note 12/16/14 (Josh Kirschner): In some of my comments below, I noted the unlikelihood of spying on iPhones that were not jailbroken. However, since many of those comments were made, certain holes were identified in iOS that exploit the iPhone's connection to trusted networks and devices to allow someone with access to the network or device to download significant amounts of personal data. Jailbreaking the iPhone was not required. Fortunately, those holes have been patched in iOS 8. For more information, see: http://www.zdziarski.com/blog/?p=3820]
Your phone is acting weirdly
Taking forever to shut off, lighting up for no reason, suddenly getting much shorter battery life or running hot when you’re not using it may indicate hidden processes are running in the background.
Your data usage skyrockets for no reason
This could be because your phone is checking in with someone else, using GPS and sending them text messages or emails that communicate where you are and what you’re doing.
What to do if you suspect your phone's being monitored
The best thing to do is perform a factory reset, which you can find as an option in your phone’s settings. Know, however, that in doing so you will lose all data stored on your phone, so back it up first.
If you’re using Apple iCloud or Android 4.0, items like your contacts, photos and music are automatically synced and saved in the cloud. But if you have an older phone, you’ll want to make sure to export your contacts before doing a factory reset. There are various ways to do this depending on what phone you’re using and which operating system it’s running. If you’re not sure, get help from your cellular provider; they can make sure to retain your contacts and other important data during a factory reset.
You'll then want to use a strong passcode to prevent unauthorized access to your device. For Android devices, you can also install an app, like AppNotifier (free on Google Play), that will email you when programs are loaded onto your phone.
(Editor's Note 9/26/12: See our updated recommendations for Android antimalware solutions)
(Editor's Note 8/28/13: See our in-depth study of mobile security apps for our latest recommendations on how to protect yourself.)
You'll then have to tackle the issue of who's doing the monitoring. Keep in mind that if your device was issued by your company or is authorized to access your company's email and other data services, you may have given your consent as part of your employment contract or when access was data access was granted.














