After a long wait and after many, many hackings, social network Twitter is finally offering its users a more secure, two-step method of identity verification.
Two-step authentication challenges you on sign-in with an extra security test before you’re allowed to use your Twitter account. When you attempt to sign in on a new device – say, on a new work computer or a friend’s laptop – you’ll be asked to verify your identity by entering your password and a six-digit numerical code. That code will be sent via SMS to your phone when you attempt to log in, so only you will have access to that number. And, ideally, that means only you will have access to your account, even if someone hacks your password.
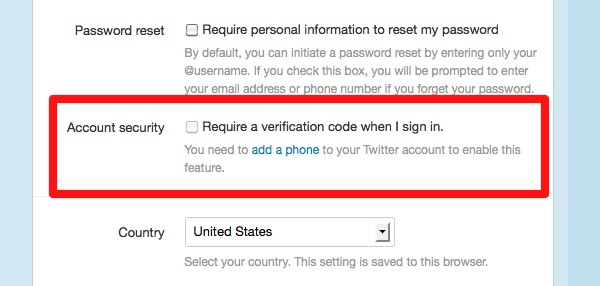
Enabling two-step authentication
To enable two-step security, sign in to your Twitter account as normal. Click the cogwheel icon in the top right-hand corner of the screen, and choose Settings from the menu that pops up. Scroll down to Account Security, and click to enable two-step security. You will need to add and verify your mobile phone number to your Twitter account if you haven’t already.
Two-step authentication will come in especially handy for major news organizations, many of whom have suffered embarrassing hackings as of late. Just last week, the Syrian Electronic Army, a digital terrorism group, hacked the Twitter feed of the The Financial Times to post propaganda in support of Syrian President Bashar al-Assad. Other recent Twitter targets of Syrian hackers include news parody publication The Onion and the CBS television network.
Twitter is one of the last major social networks to offer a more secure login. Google’s two-step authentication has been live since 2011. Facebook’s offers a similar two-step method called login approvals, which has also been available for a couple years.













