The fresh start of a new year is ideal for rethinking how we use the technology in our daily lives, whether it’s for better efficiency, security, or, more crucially than ever, privacy.
In 2018, it wasn’t only tech giants that made headlines for data breaches, large-scale hacks and other privacy missteps. Billions of people were affected by cyber attacks on major brands including hotel groups, airlines and retailers, with the increase in the number of hacks outstripping similar periods the year before.
Good digital habits are half the battle in protecting our privacy from hackers as well as the corporations whose revenue relies on targeted advertising based on our personal information – but equally crucial is an overhaul of how our data is managed by institutions from tech giants to governments. New legislation such as Europe’s General Data Protection Regulation (GDPR) represents the beginnings of this overhaul – and in the meantime, we can also choose to use our technology differently.
Here are nine resolutions for 2019 to revamp our relationship with technology:
1. Reconsider how you use Facebook (and whether you should use it at all)
Yes, Facebook is where many of us get our news, post our family photos and organize events. But the social giant’s seemingly ceaseless string of privacy scandals in 2018 has revealed the extent to which Facebook has allowed its users’ personal information to be leveraged by other companies – such as sharing access to private messages with third-parties including Spotify and Microsoft (something it disputes is an issue), and its infamous association with political consultancy Cambridge Analytica, which was able to access the information of not only users of a particular app, but all their friends’ information as well, using this data to influence the 2016 presidential election.
Digging into those Facebook privacy settings can help reclaim some control over what information you’re sharing with friends as well as Facebook’s vast, shadowy bulk of advertisers, but it doesn’t address the crux of the issue with Facebook: it’s not only someone’s own Facebook data that is at risk from inadvertent oversharing but their friends’ and even contacts who are not even on Facebook.
If you feel it’s time to cut ties with the big and not-so-friendly social giant, here’s where to start deleting your Facebook account.
2. Stop oversharing with Google
Facebook isn’t the only tech giant to have exposed its voracious appetite for user data. Google also offers its third-party developers access to Gmail and Google accounts, while many of its services on Android and iOS smartphones continue to track and store location data even when users disable the setting. One study found that its Android services are designed to manipulate users into accepting location tracking, thus allowing it to process the vast amounts of incredibly detailed and intimate data inherent in someone’s real-time location.
If that creeps you out, you may want to begin minimizing the extent of data Google can extract from you. For me, that starts with its primary and biggest business: search. Instead of Google, I’ve begun almost exclusively using DuckDuckGo, a privacy-focused search engine that does not track searches and thus cannot build a profile of a user for leverage in advertising. Searching anonymously also prevents that controversial filter bubble of results, where search results are tailored to someone’s past clicks and perceived preferences.
Because using DuckDuckGo on Chrome (my previous browser of choice) can still result in these searches being sent back to Google, I’ve also switched to Firefox, an equally fast browser that offers several tools to protect privacy online.
If you find yourself missing Google’s results, you can use a neat DuckDuckGo feature called ‘bangs’, which allows you to type ! followed by ‘g’ then the search query in order to see what Google would turn up. (You can also use this feature to directly search thousands of other domains.)
3. Use only strong passwords
As a savvy reader of Techlicious, it’s likely none of your passwords are among these clangers of 2018. Still, if you haven’t been using a password manager, chances are there are at least one or two that aren’t as strong as they could be – and chances are very good that there are a few inactive or infrequently used accounts that share the same basic passwords. This presents a security risk as the hack of one account can reveal enough information for hackers to break into others, or to use in more sophisticated, targeted phishing scams.
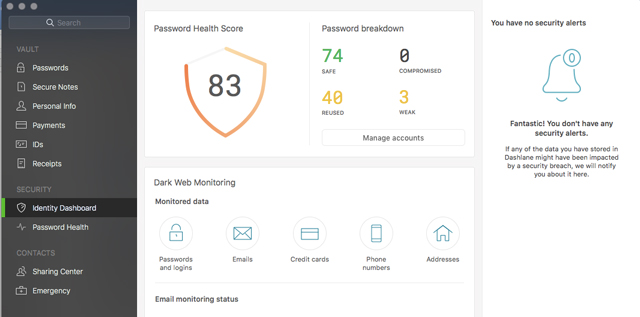
A password manager can not only help with generating strong, new passwords but also scan your existing passwords to flag reused and weak passwords. One of our favorite password managers, Dashlane, additionally offers a premium subscription feature that will search the net to find any of your accounts that have been hacked and if the login is for sale on the Dark Web. If like me, you discover your details have been compromised in various breaches of tech services over the last several years, Dashlane will flag these for immediate updating.
4. Use a VPN
With U.S. ISPs given the federal greenlight to use and sell their users’ data for advertising, now is the time to start protecting your web traffic. Virtual private network (VPN) software scrambles your IP address, encrypts all data sent between your computer and the sites you visit, and masks your true location and service provider.
That’s of special importance if you often use public Wi-Fi, as a VPN will prevent hackers, snoops or a dodgy hotspot operator from seeing your traffic and potentially scraping sensitive information such as financial details.
Everyday use of a VPN can also offer a measure of anonymity as internet searches and site visits are less readily linked to your profile (that is, your computer’s unique address). You may not, for example, want searches for a medical condition to be used in targeted advertising.
Two of our favorites are NordVPN and ExpressVPN.
5. Turn on two-factor authentication for your accounts
As far as free high-security features go, two-factor authentication (2FA) is a no-brainer. It adds an extra layer of protection from hackers by requiring a code or additional approval on top of a potentially crackable password.
Yet as of last year, less than ten percent of Gmail users had implemented 2FA, which means even relatively tech-savvy people were not using this security feature. What’s more, those who did, often chose SMS as their second factor (where a text message containing a unique code is sent to the user’s phone). However, this particular method is no longer considered safe. Hackers have been able to intercept such messages – as occurred with last year’s Reddit breach. In other cases, genuine two-factor SMSes have been followed up with phishing messages that asked users to reply with the code they had just received.
A more secure method is to download an authenticator app (such as Google Authenticator (Android/iOS) or Microsoft Authenticator (Android/iOS) which can be linked to dozens of accounts, such as Google, LastPass, Twitter and many more. The app then generates time-sensitive two-factor codes to input with your password. You might even want to splash out for a dedicated two-factor physical key, such as the Yubikey ($50, check price on Amazon), which can generate one-time codes as well as offer a password-free tap-to-login for Microsoft accounts.
6. Declutter your technology
Getting rid of duplicate files, unneeded program executables and other fragments of everyday use can speed up an old laptop, so arm yourself with our guide to cleaning out your computer and get in there. That goes for your smartphone too. If your smartphone has been slowing down, a deep-clean of its storage could tide you over until your next upgrade. Chances are you’ll find scores of photos you don’t need and apps you never use, so get deleting.
Bonus: deleting unused apps improves security and privacy by removing potential areas for data leaks or hacks, especially as underused apps tend to be overlooked when you’re installing those software updates to patch bugs and vulnerabilities.
7. Use Amazon more ethically
As a long-time Prime subscriber, I’m well acquainted with the conveniences of two-day, next-day, and, sometimes, two-hour delivery. On more than a few occasions, I’ve made up for poor planning by purchasing birthday presents on Amazon – but as the big A announces its second and third U.S. headquarters in one fell swoop, I’m confronted by the reality of how such convenience is wrought: by express delivery vehicles that clog up city centers and raise emissions, often half-empty because companies don’t have the time to consolidate other orders – which also puts more trucks on streets.
While it would be nice to resolve to only purchase in local shops, perhaps a more realistic solution is to select three-to-five-day delivery when a parcel’s instantaneous arrival isn’t absolutely necessary. Bonus: Amazon rewards this more sustainable choice with a variety of credit offers, including a $1 credit towards Kindle books and audiobooks.
8. Unplug more often
According to a 2018 Nielsen study, American adults spend more than 11 hours every day listening to, watching, reading and interacting with media. Of those 11 hours, 3 hours and 48 minutes are spent on computers, smartphones and tablets. Blue light emitted by our devices is particularly damaging, shortening the duration and quality of sleep, according to a new study conducted at the University of Haifa and published in the journal Chronobiology International.
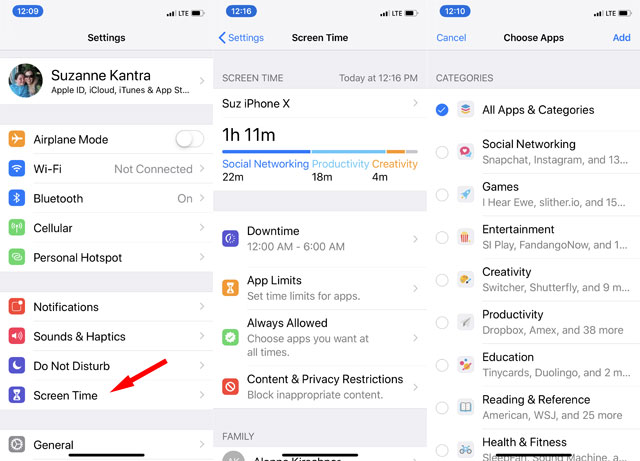
So make use of Apple's Screen Time (available in Settings for iOS 12) and Google's Digital Wellbeing (included in Android Pie, and free on Google Play for earlier versions of Android) to gain awareness of how much time you're spending on your devices and set time limits. You can also use the apps to remind you to unplug at night with the Wind Down mode for Digital Wellbeing and Downtime for Screen Time.
9. Read Terms & Conditions
Keeping tabs on the terms and conditions of new and existing accounts helps you make a decision about whether you are happy to keep using a service – and when installing new apps or creating new accounts, it helps to understand how much information you’re really giving away.
As Europe’s General Data Protection Regulation (GDPR) took effect last year, many U.S. sites with European audiences have also had to take steps to be compliant with this ground-breaking legislation for how companies must handle user data.
You're probably familiar with the consent screens many sites are now presenting, which display the various trackers that are logging visitors’ data. It’s worth reading through those screens before hitting accept. For example, you might want to disable third-party ad trackers from data brokers you’ve never heard of, but allow trackers for content recommendation.
Indeed, the most reputable sites tend to offer visitors an easy way to reject all but necessary trackers (like holding your shopping cart items while you browse for items) – and in contrast, far too many sites pay lip service to the spirit of GDPR compliance by displaying a list of hundreds of third-party ad trackers that must be rejected one by one. If it’s not necessary to visit such sites – and you don’t wish to spend five minutes unchecking over 400 checkboxes (which I have done, to make a point) – you may prefer to consider “spending” your clicks at sites that are making a better effort to be transparent and, yes, honorable about handling your information.
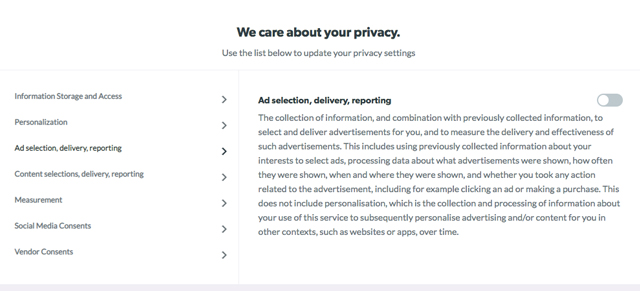
With lawmakers discussing the potential for a U.S. version of the GDPR, the days for companies making a land grab for personal data could be numbered – and we can help set that precedent by choosing wherever possible how we accept our data to be used.
[image credit: 2019 loading concept via BigStockPhoto]












